Strategy and Governance
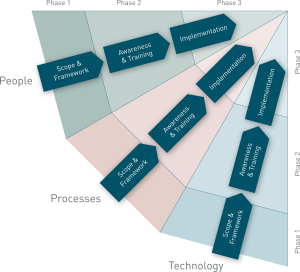
Challenges often arise with regard to GRC-related processes, technologies and overall programs embedded within an organisations IT and business enterprise architecture. Multiple decentralized GRC programs may lead to inconsistency in deployment and configuration of technologies, and misalign GRC policies and procedures with business strategy.
An effective and mature GRC program is one that has proper business requirements as well as the right blend of automation and technology support.
A strong cyber security strategy should align to the business vision, objectives and innovation projects. If implemented effectively, it can enhance product integrity, customer experience, operations, regulatory compliance, brand reputation, investor confidence and more — leading to a return on your cyber investments.
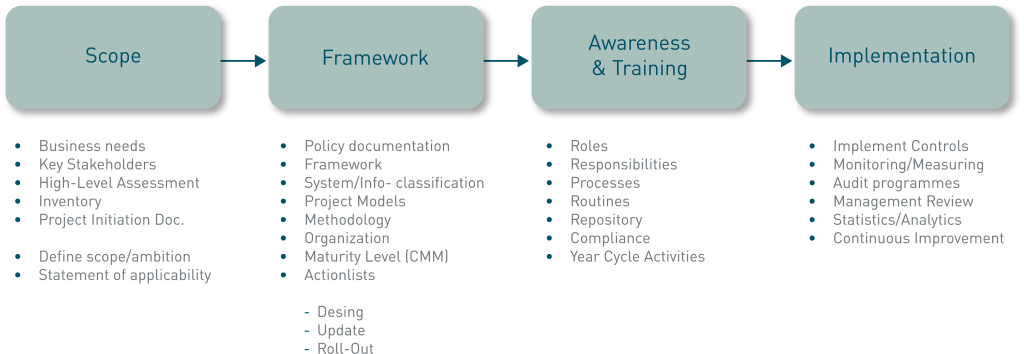
Build a road map to create and implement the right GRC operating model
- Define compliance, business and IT future-state requirements
- Current status automation and technology, costing model and value return assessments
- Develop a business case and road-map
- Create a dynamic business case that can be used as an operational tool to document program operating model and success factors
- Identify a path (i.e., a road map) for building out the target operating model, including project scope, timeline and technology deployment plan
- Test and verify the GRC target operating model
- Verify functionality and performance by working with business and IT organizations
- Define and execute the go-live procedures through working with the GRC program stakeholders and deploying the new technologies, data model and processes
Contact us today!