Penetration Testing
When was the last time you tested the defenses in place and the security architecture of your networks, applications and services to find the vulnerabilities, which are putting your data, your customers and their data at risk?
Our professional and certified penetration testers will subject your targets to a structured methodology to uncover as many vulnerabilities as possible during the engagement window.
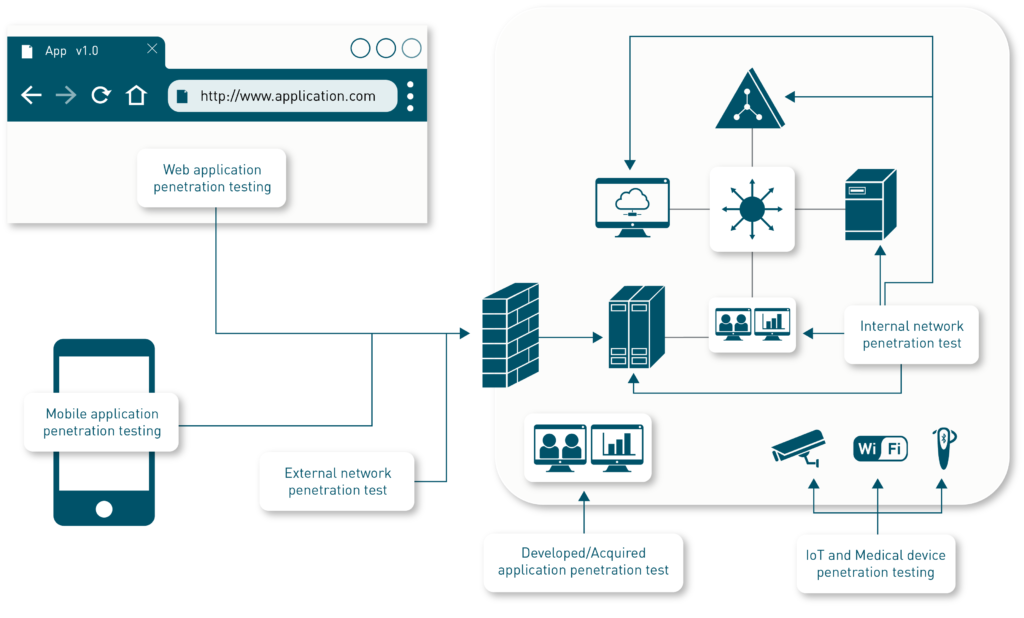
Zacco Digital Trust can perform penetration tests of:
- Mobile Applications – Android and iOS
- Web Applications – All languages and frameworks
- Internal and External networks – All types, ipv4, ipv6, LAN, Wi-Fi
- Developed or acquired applications – PC-applications, Web Applications, Linux, Mac OS
- IoT and Medical Devices
If you fall within or implement any of these regulations and compliance standards – you should be performing regular penetration tests:
- ISO27001 ISMS
- AICPA System and Organization Controls 2 (SOC2)
- Payment Card Industry Data Security Standard (PCI DSS)
- GDPR Compliance
- NIS Directive & Regulations
- NHS DSP Toolkit
- SWIFT CSP
- The Food and Drug Administration (FDA)’s medical device penetration testing regulations
- HIPAA Evaluation Standard § 164.308(a)(8)
- FINRA – The Securities Exchange Act of 1933 (17 CFR §240.17a-4(f))
Our penetration testing methodology
Zacco Digital Trust follows industry best practices and ensures that your networks, applications and services are tested in adherence with PTES, OSSTMM, NIST SP800-115, ISSAF, and OWASP Application Security Verification Standard. The ASVS level (1-3) used during testing is agreed upon during initial scoping (when applicable).
All identified vulnerabilities are documented extensively with their own chapters containing the following:
- Description: the vulnerability description with screenshots, commands, example code and explanatory text.
- Severity level: the threat level that Zacco considers this to have on the assessment target. The scale is based on the standardized Common Vulnerability Scoring System (CVSS) version 3.1 and has the following ranges: Critical, High, Medium, Low and Informational.
- Impact: an impact description detailing the effect of the vulnerability on the assessment target if an adversary manages to exploit the described vulnerability.
- Recommendations: Detailed recommendations on one or more options of mitigating the described finding.
Each vulnerability is ranked to make it easier for the customer to put their efforts on the highest risk-inducing vulnerability.
The report is delivered digitally and orally.
What you get:
- Help to find and understand the vulnerabilities in your solutions or infrastructure
- A first-class report which details the vulnerabilities, their impact, and how to mitigate them
- Certified and professional penetration testers
Contact us today!